Introduction
Many software programs must establish connections to third-party services in order to accomplish their goals. The majority of applications need to communicate with other programs, either by sending messages or by using application programming interfaces.
However, as a growing number of individuals migrate their apps to Kubernetes, it’s getting more difficult to provide safe and dependable access to them. Network traffic may have trouble getting where it needs to go due to the presence of several deployments as well as services.
Kubernetes is a well-liked open-source system for controlling containerized software. To make your Kubernetes applications accessible to consumers, you must expose it to the internet. Both neither an Ingress controller nor a Load Balancer will do the trick here.
What is Kubernetes?
A Kubernetes service can benefit from an Ingress controller’s superior routing as well as traffic management features. It provides name-based virtualized hosting, supports SSL termination, as well as routes traffic depending on URI path. Web applications as well as microservices that have several endpoints are two examples of applications that might benefit from an Ingress controller’s sophisticated traffic management as well as routing capabilities.
If you want to become a certified Kubernetes professional then enroll in MindMajix’s Kubernetes Certification Training.
What is Ingress?
Ingresses are a means to control the incoming traffic to the Kubernetes cluster. They aid in directing requests to the appropriate location, ensuring that your program has access to the data it requires. Here, you can examine two of these mechanisms—ingresses as well as load balancers—in this lesson.
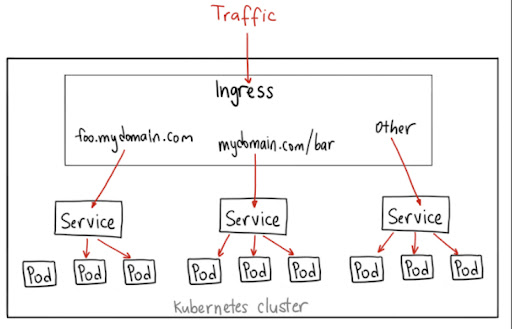
Difference between Kubernetes load balancer vs Ingress
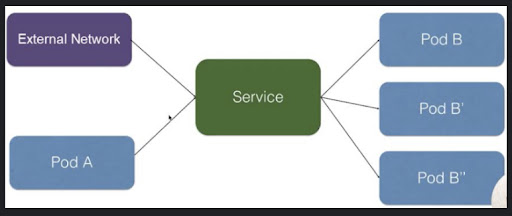
LoadBalancer
Exposing a service over the internet typically involves using a LoadBalancer. It will start a Network Load Balancer on GKE and assign a single IP address to the service you are running, which will then receive all traffic.
This is the standard procedure for making a service publicly available. The service gets all connections made to the given port. No routing or filtration is taking place, etc. This means you can connect to it using a wide variety of protocols, such as HTTP, TCP, UDP, Websockets, gRPC, and so on.
The major drawback is that each accessible service has its own unique IP address as well as a separate LoadBalancer, that can quickly mount up in cost.
Ingress
Contrary to popular belief, Ingress is not a service. However, it acts as a gateway or “smart router” in front of many services in your cluster.
There is a wide variety of Ingress controllers, each with its own set of features and powers.
The GKE ingress administrator, by default, will launch an HTTP(S) load balancer on your behalf. This will allow you to route requests to the backend services based on a subdomain as well as a path. For instance, you can direct traffic to the foo service by sending it to foo.yourdomain.example, and traffic to your bar service by directing it to yourdomain.example/bar/path.
While Ingress is the most effective method for making your services public, it is also the most complex. The Google Cloud Load Balancer is just one example of an Ingress controller; others include Nginx, Contour, Istio, and others. Ingress controllers have add-ons, such as the cert-manager, that allow automated SSL certificate provisioning for your services.
Table Summary of Main Distinctions Between LoadBalancer and Ingress
| Aspect | Kubernetes Load Balancer | Ingress |
| Type | Kubernetes service type with built-in cloud provider LB | Kubernetes resource managing HTTP(S) routing |
| Layer | L4 (TCP/UDP) | L7 (HTTP/HTTPS) |
| Traffic Routing | Primarily TCP/UDP traffic, not HTTP | Advanced HTTP-based routing |
| Use Cases | Suitable for non-HTTP services, external TCP/UDP traffic | Ideal for HTTP applications, web services |
| Customization | Limited to cloud provider-specific features | Highly configurable with path and host rules |
| Resource Type | Service with LoadBalancer type | Ingress resource |
| SSL/TLS Termination | At the service level (not always available) | At the Ingress level |
| Path-Based Routing | Not directly supported | Supported via Ingress rules |
| Host-Based Routing | Limited via service DNS names (no HTTP-specific routing) | Supported via Ingress rules |
| Header-Based Routing | Not supported | Supported via Ingress annotations |
| Backend Service | Typically maps to a single service | Can route to multiple services using rules |
| Scalability | Scales with service instances | Single Ingress controller for many Ingress resources |
| Ingress Controllers | Not applicable, uses cloud provider LB | Various controllers available (e.g., Nginx, Traefik) |
| Affordability | Costly due to cloud provider LB charges | Cost-effective (controller-specific) |
| Logging/Analytics | Limited | Can be integrated with various tools |
| Ingress Providers | Provider-specific (e.g., GKE, AWS) | Controller-specific (e.g., Nginx, Traefik) |
| Complexity | Simpler setup, fewer features | More complex, offers advanced features |
| Portability | Limited to specific cloud providers | Can be used across various Kubernetes clusters |
| Community Support | Varies based on cloud provider | Strong open-source community support |
| Health Checks | Supported through service settings (readinessProbe) | Supported through Ingress controllers |
| High Availability | Managed by cloud providers | Configuration varies by controller |
| Service Discovery | Limited to Kubernetes service discovery (DNS-based) | Can integrate with external service discovery |
| Web Application Firewall (WAF) | Depends on cloud provider features | Can be implemented using specific Ingress controllers |
| Rate Limiting | Typically not provided by cloud provider LB | Can be configured using Ingress controller features |
With this updated table, you can see how Kubernetes Load Balancer as well as Ingress stack up against one another in terms of routing, customisation, scalability, and other characteristics. Always consider your unique needs and network configuration when deciding between a Load Balancer as well as Ingress.
Kubernetes Load Balancer vs. Ingress in Several Fields
1. Purpose
Kubernetes Load Balancer: By configuring LoadBalancers in the cloud, it is possible to make services accessible from the outside world. It routes data packets (TCP/UDP) to the appropriate cluster services.
Ingress: The ingress controller handles HTTP(S) load balancing as well as routing. You can set up rules based on host names and paths to direct HTTP requests to specific services.
2. Layer
Kubernetes Load Balancer: Handles TCP/UDP traffic and functions at Layer 4 (the transport layer). It does not look at the data inside of packets.
Ingress: Functions only with HTTP/HTTPS traffic and works at Layer 7 (the application layer). It examines HTTP headers, routes, and hostnames to determine how to direct traffic.
3 .Redirecting Traffic
Kubernetes Load Balancer: Routes data at the transport layer, which makes it usable with protocols other than HTTP. It lacks support for complex HTTP-based routing.
Ingress: Provides sophisticated HTTP routing, making it a good fit for web-based applications. It may redirect data depending on hostnames, paths, as well as header information.
4. The Termination of SSL/TLS
Kubernetes Load Balancer: In Kubernetes, SSL/TLS termination is often handled by the service and not the Load Balancer. The answer to this question is cloud provider-specific.
Ingress: It is possible to specify SSL/TLS termination at the Ingress level, making it easier to keep track of and deploy certificates as well as other security measures.
5. Customization
Kubernetes Load Balancer: Only features as well as settings that are unique to a given cloud service provider are modifiable in a Kubernetes load balancer.
Ingress: Path as well as host rules, annotations, including controller-specific capabilities all contribute to Ingress’s flexible configuration options. It offers a wide range of customization options.
6. Server-Side Support
Kubernetes Load Balancer: Load Balancer for Kubernetes In most cases, this corresponds to a single cluster service.
Ingress: Intrude Uses rules as well as path-based routing to send traffic to numerous services inside the cluster.
7. Advanced Pathfinding
Kubernetes Load Balancer: It cannot handle path-based or header-based routing via HTTP.
Ingress: Ingress is flexible enough to handle advanced deployment scenarios because of its assistance with path-based routing, host-based routing, as well as header-based routing.
8. Scalability
Kubernetes Load Balancer: The total number of service instances does not matter to the Kubernetes load balancer.
Ingress: Intrude As a general rule, it is more scalable to have a single Ingress controller that handles routing for several Ingress resources.
9. Invasion Control Units
Kubernetes Load Balancer: Using Ingress controllers is not required. uses LoadBalancers from a cloud provider.
Ingress: Nginx, Traefik, and other Ingress controllers are necessary for Ingress to operate. Those controllers are in charge of the routing as well as the load distribution.
10. Affordability
Kubernetes Load Balancer: Load Balancer for Kubernetes LoadBalancer fees charged by your cloud provider can add up.
Ingress: Intrude can save you money, albeit how much you save depends on the Ingress controller you end up buying.
11. Portability
Kubernetes Load Balancer: is limited in its portability because it is dependent on a single cloud provider.
Ingress: Intrude Provides increased mobility by being used on many Kubernetes clusters.
12. Community Support
Kubernetes Load Balancer: Different cloud service providers may or may not offer support for Kubernetes load balancers.
Ingress: Intrude Benefits from extensive documentation and widespread open-source support, as well as a wide selection of controllers.
There are two parts to a Kubernetes cluster, the Kubernetes Load Balancer along with the Ingress, since they each perform different functions and have unique capabilities. The optimal choice depends on your specific circumstances and the make-up of your current system.
Conclusion
Kubernetes services as well as Ingress controllers are two of the most important components in directing internet traffic to the cluster. Ingress centralizes the controller’s routing rules into a single resource. We may give the workloads access to HTTP routing by positioning Ingress in front of the services. But first, you’ll need to configure the controller to work with your cluster.
In contrast, services are a high-level abstraction for making networked pods accessible. NodePort services are utilized for development or as a substitute to internal services for providing both TCP and UDP communication within the cluster. Last but not least, a load balancer is tough to self-host but can deal with any kind of traffic and is totally handled by the cloud provider.
All of these solutions aid Kubernetes in efficiently onboarding workloads, but which one is ideal for a given scenario varies.

